1. 2020/cloudflare
https://blog.cloudflare.com/sad-dns-explained/
SAD DNS Explained
11/14/2020
- Marek Vavruša Nick Sullivan
As part of a coordinated disclosure effort earlier this year, the researchers contacted Cloudflare and other major DNS providers and we are happy to announce that 1.1.1.1 Public Resolver is no longer vulnerable to this attack.
In this post, we’ll explain what the vulnerability was, how it relates to previous attacks of this sort, what mitigation measures we have taken to protect our users, and future directions the industry should consider to prevent this class of attacks from being a problem in the future.
1.1. Defeating Source Port Randomization via ICMP error messages
Another way to defeat the source port randomization is to use some measurable property of the server that makes the source port easier to guess.
If the attacker could ask the server which port number is being used for a pending query, that would make the construction of a spoofed packet much easier.
No such thing exists, but it turns out there is something close enough - the attacker can discover which ports are surely closed (and thus avoid having to send traffic).
One such mechanism is the ICMP “port unreachable” message.
Let’s say the target receives a UDP datagram destined for its IP and some port, the datagram either ends up either being accepted and silently discarded by the application, or rejected because the port is closed.
If the port is closed, or more importantly, closed to the IP address that the UDP datagram was sent from, the target will send back an ICMP message notifying the attacker that the port is closed.
This is handy to know since the attacker now doesn’t have to bother trying to guess the pending message ID on this port and move to other ports.
A single scan of the server effectively reduces the search space of valid UDP responses from 232 (over a billion) to 217 (around a hundred thousand), at least in theory.
This trick doesn’t always work.
Many resolvers use “connected” UDP sockets instead of “open” UDP sockets to exchange messages between the resolver and nameserver.
Connected sockets are tied to the peer address and port on the OS layer, which makes it impossible for an attacker to guess which “connected” UDP sockets are established between the target and the victim, and since the attacker isn’t the victim, it can’t directly observe the outcome of the probe.
To overcome this, the researchers found a very clever trick:
they leverage ICMP rate limits as a side channel to reveal whether a given port is open or not.
ICMP rate limiting was introduced (somewhat ironically, given this attack) as a security feature to prevent a server from being used as an unwitting participant in a reflection attack.
In broad terms, it is used to limit how many ICMP responses a server will send out in a given time eriod.
Say an attacker wanted to scan 10,000 ports and sent a burst of 10,000 UDP packets to a server configured with an ICMP rate limit of 50 per second, then only the first 50 would get an ICMP “port unreachable” message in reply.
Rate limiting seems innocuous until you remember one of the core rules of data security: don’t let private information influence publicly measurable metrics.
ICMP rate limiting violates this rule because the rate limiter’s behavior can be influenced by an attacker making guesses as to whether a “secret” port number is open or not.
don’t let private information influence publicly measurable metricsAn attacker wants to know whether the target has an open port, so it sends a spoofed UDP message from the authoritative server to that port.
If the port is open, no ICMP reply is sent and the rate counter remains unchanged.
If the port is inaccessible, then an ICMP reply is sent (back to the authoritative server, not to the attacker) and the rate is increased by one.
Although the attacker doesn’t see the ICMP response, it has influenced the counter.
The counter itself isn’t known outside the server, but whether it has hit the rate limit or not can be measured by any outside observer by sending a UDP packet and waiting for a reply.
If an ICMP “port unreachable” reply comes back, the rate limit hasn’t been reached.
No reply means the rate limit has been met.
This leaks one bit of information about the counter to the outside observer, which in the end is enough to reveal the supposedly secret information (whether the spoofed request got through or not).
Diagram inspired by original paper 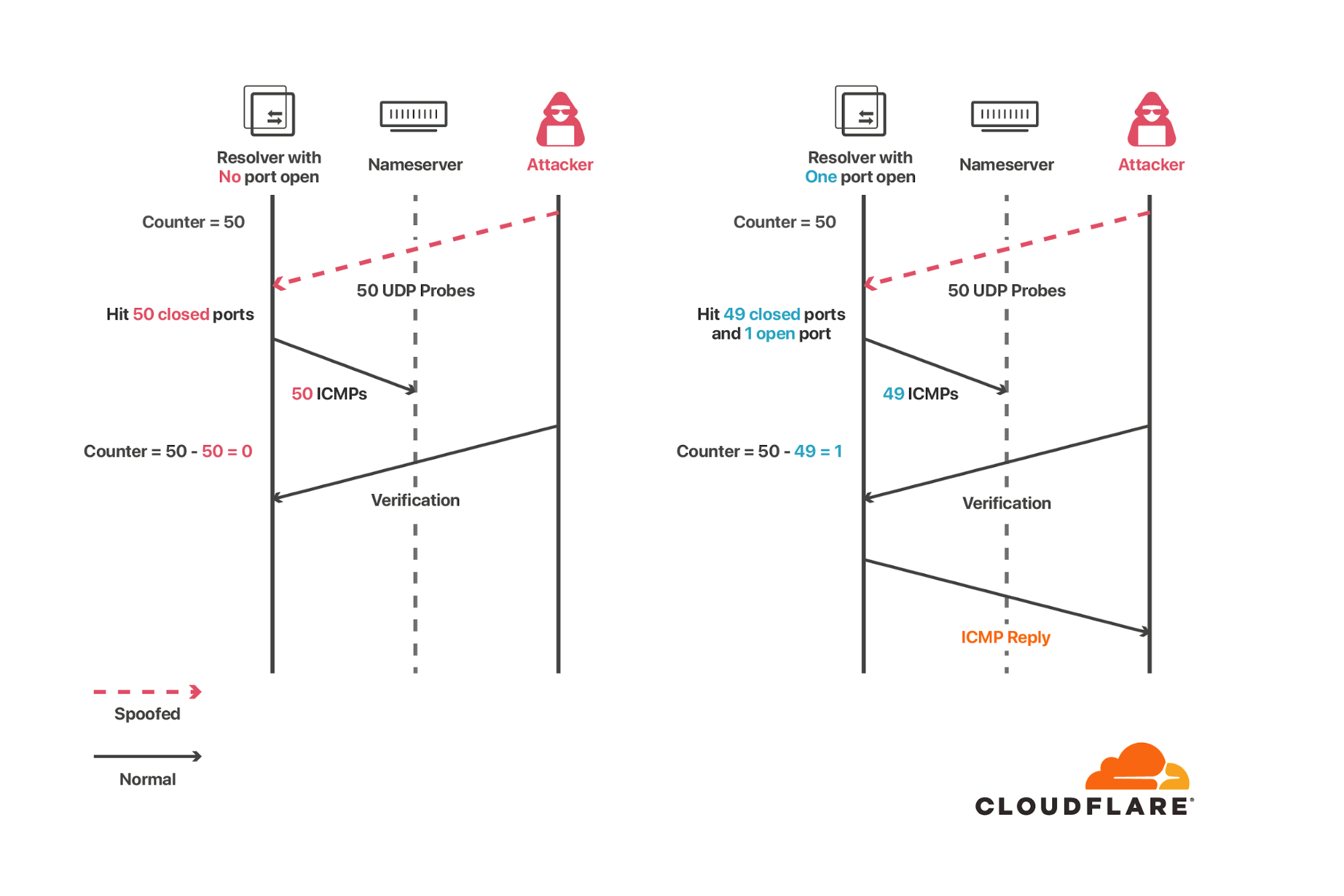
Concretely, the attack works as follows:
the attacker sends a bunch (large enough to trigger the rate limiting) of probe messages to the target, but with a forged source address of the victim.
In the case where there are no open ports in the probed set, the target will send out the same amount of ICMP “port unreachable” responses back to the victim and trigger the rate limit on outgoing ICMP essages.
The attacker can now send an additional verification message from its own address and observe whether an ICMP response comes back or not.
If it does then there was at least one port open in the set and the attacker can divide the set and try again, or do a linear scan by inserting the suspected port number into a set of known closed ports.
Using this approach, the attacker can narrow down to the open ports and try to guess the message ID until it is successful or gives up, similarly to the original Kaminsky attack.
In practice there are some hurdles to successfully mounting this attack.
First, the target IP, or a set of target IPs must be discovered. This might be trivial in some cases - a single forwarder, or a fixed set of IPs that can be discovered by probing and observing attacker controlled zones, but more difficult if the target IPs are partitioned across zones as the attacker can’t see the resolver egress IP unless she can monitor the traffic for the victim domain.
The attack also requires a large enough ICMP outgoing rate limit in order to be able to scan with a reasonable speed. The scan speed is critical, as it must be completed while the query to the victim nameserver is still pending. As the scan speed is effectively fixed, the paper instead describes a method to potentially extend the window of opportunity by triggering the victim's response rate limiting (RRL), a technique to protect against floods of forged DNS queries. This may work if the victim implements RRL and the target resolver doesn’t implement a retry over TCP (A Quantitative Study of the Deployment of DNS Rate Limiting shows about 16% of nameservers implement some sort of RRL).
Generally, busy resolvers will have ephemeral ports opening and closing, which introduces false positive open ports for the attacker, and ports open for different pending queries than the one being attacked.
We’ve implemented an additional mitigation to 1.1.1.1 to prevent message ID guessing - if the resolver detects an ID enumeration attempt, it will stop accepting any more guesses and switches over to TCP. This reduces the number of attempts for the attacker even if it guesses the IP address and port correctly, similarly to how the number of password login attempts is limited.